The only MFA built on Zero Trust principles.
Majority of breaches now originate with some form of credential compromise. Attackers have shifted focus to compromising user credentials as opposed to exploiting vulnerabilities or weaknesses in systems and applications.
Offered as a service, Block Armour’s UniAuth solution has the unique distinction of being a plug and play unified MFA solution. It can easily be deployed in a few hours and does not require changes in application code. The solution creates a unified authentication overlay across your IT ecosystem, irrespective of whether applications are hosted in a data center, cloud and/or multi-cloud environment.
The key benefits of the solution are:
1
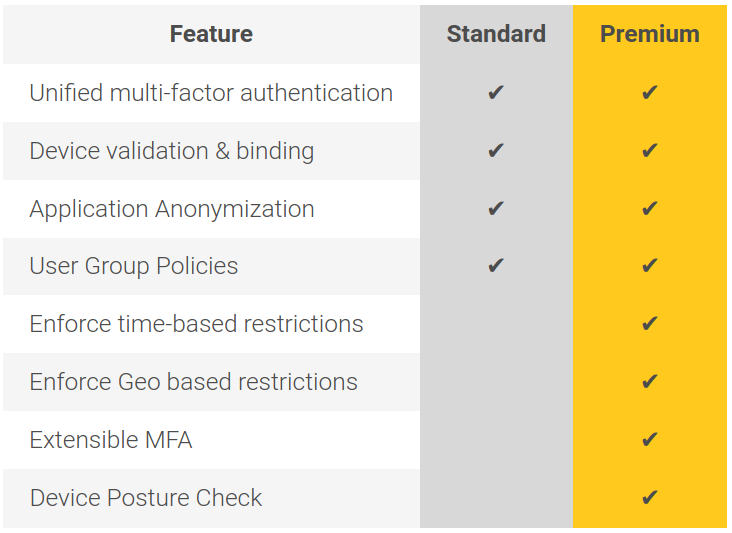
Unified authentication for users logging in to on-premise, cloud and SAAS applications.
Unification of all your MFA needs irrespective of the application type or where it is deployed.
2
Device validation and binding
Access permitted only from authorized and compliant devices. Allows binding of user with specific devices.
3
Enforce Time-based restrictions
User access can be restricted based on time.
4
Enforce Geo-location based restrictions
Access to applications can be restricted from specific countries.
5
Device Posture Check
Choose from over 15 posture checks which can be evaluated on the device from which login has been requested, such as updated anti-virus, installed patches etc.
6
Block login requests from rogue devices
Login is permitted only from trusted devices. Requests from rogue devices are automatically blocked.
7
Extensible MFA
MFA capability can be extended for protecting access to SSH or RDP logins with the click of a button and without the need to deploy a separate radius server as well as other overheads caused due to integration challenges.
8
Application Anonymization
Create a Software Defined Perimeter (SDP) to protect the application by rendering it invisible.
9
Integration support
10
Focus on your business growth
The solution is delivered as a service and fully managed by us, freeing up time for customer IT and security teams to focus on business priorities.