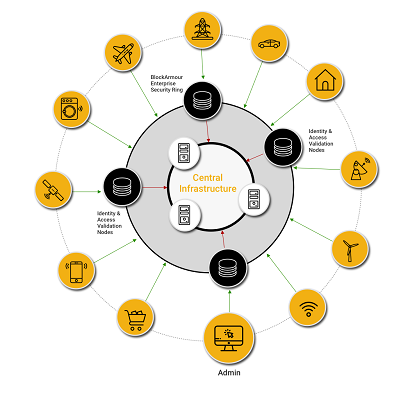
Security for today's hybrid and distributed enterprise-IT environments
Enabling ‘assets everywhere’ and ‘access from anywhere’
The rapid adoption of Cloud technology and employees working remotely has resulted in highly distributed and hybrid IT ecosystems. Cyberattacks are on the rise and legacy approaches and tools are simply unable to deliver comprehensive cybersecurity for today’s modern enterprise-IT environments. Caught recently by the sudden onslaught of COVID-19, many organizations have inadequate security to support remote work and are dealing with wider attack surfaces and less secured user devices. Meanwhile, traditional security platforms continue to get compromised and expose critical systems.
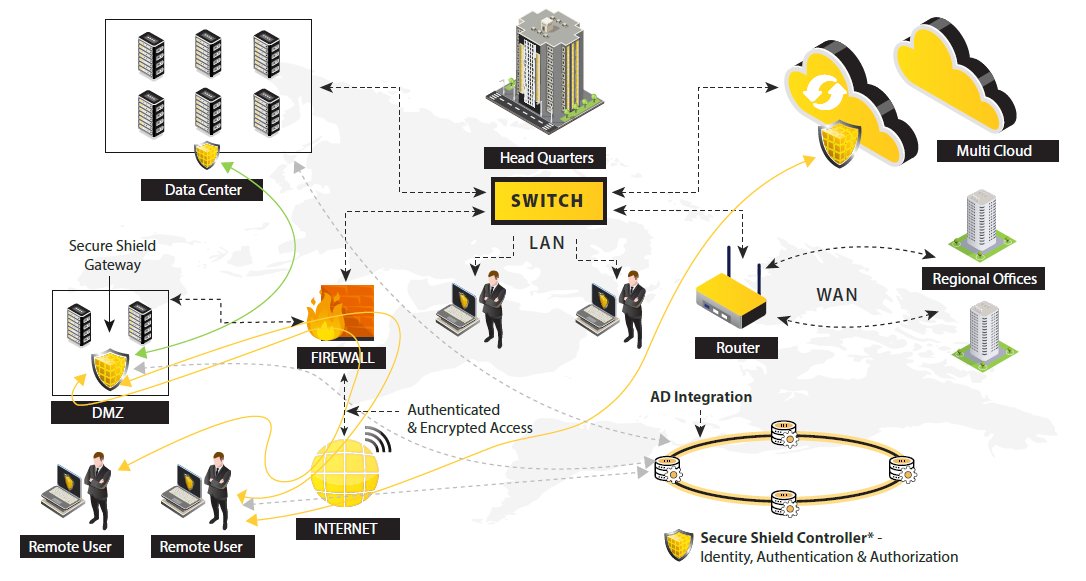
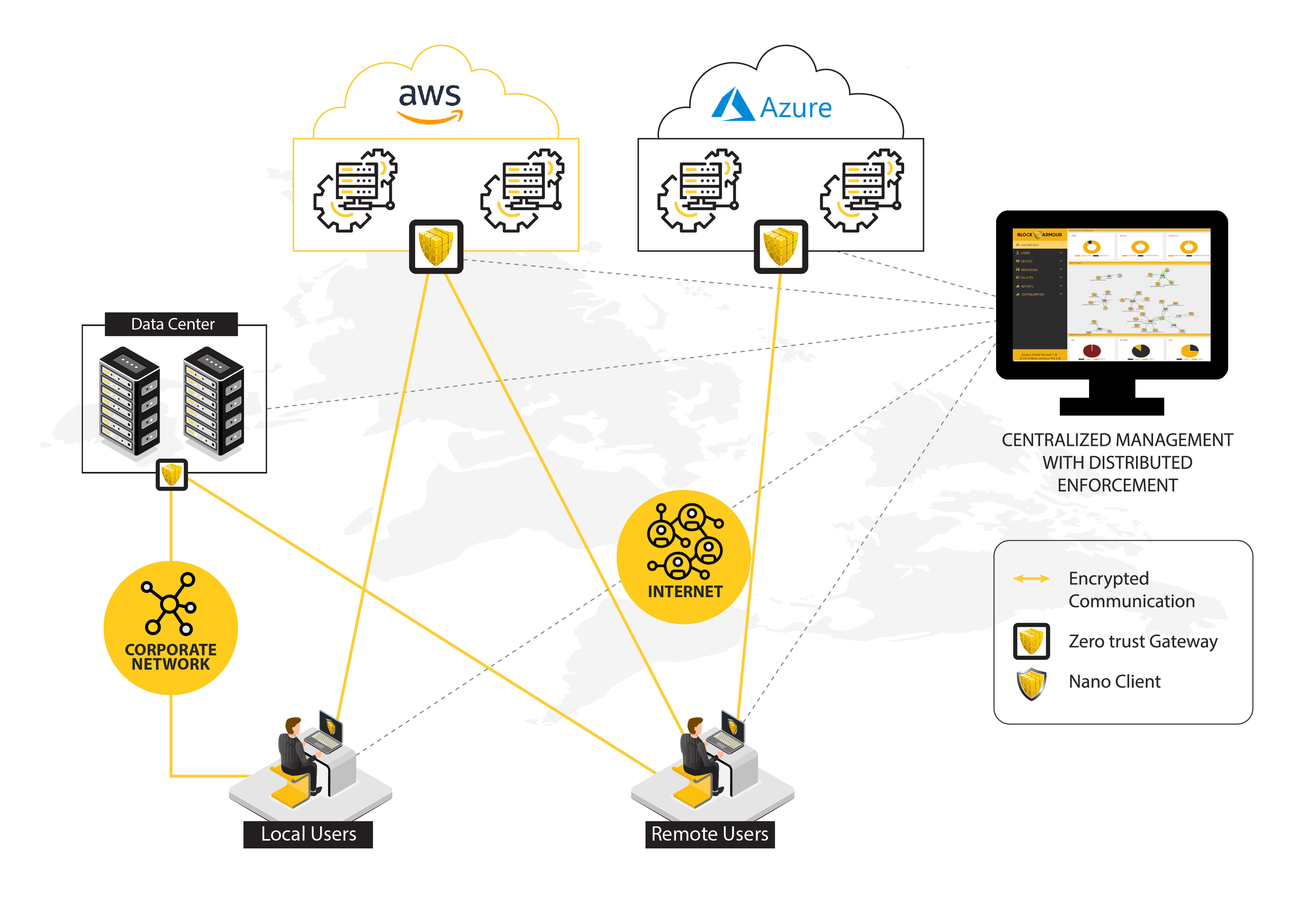
Zero Trust based
Data from a recent State of the Cloud Report shows that nine in 10 enterprises are taking a multi-cloud strategy approach. Within that group, more than 80% of enterprises report having a hybrid cloud strategy in place. Multi-cloud environments add complexity and security challenges. And, organizations have struggled to implement proper Cloud security. Data from IDC shows that 98% of organizations experienced a Cloud Security Breach in past 18 months.
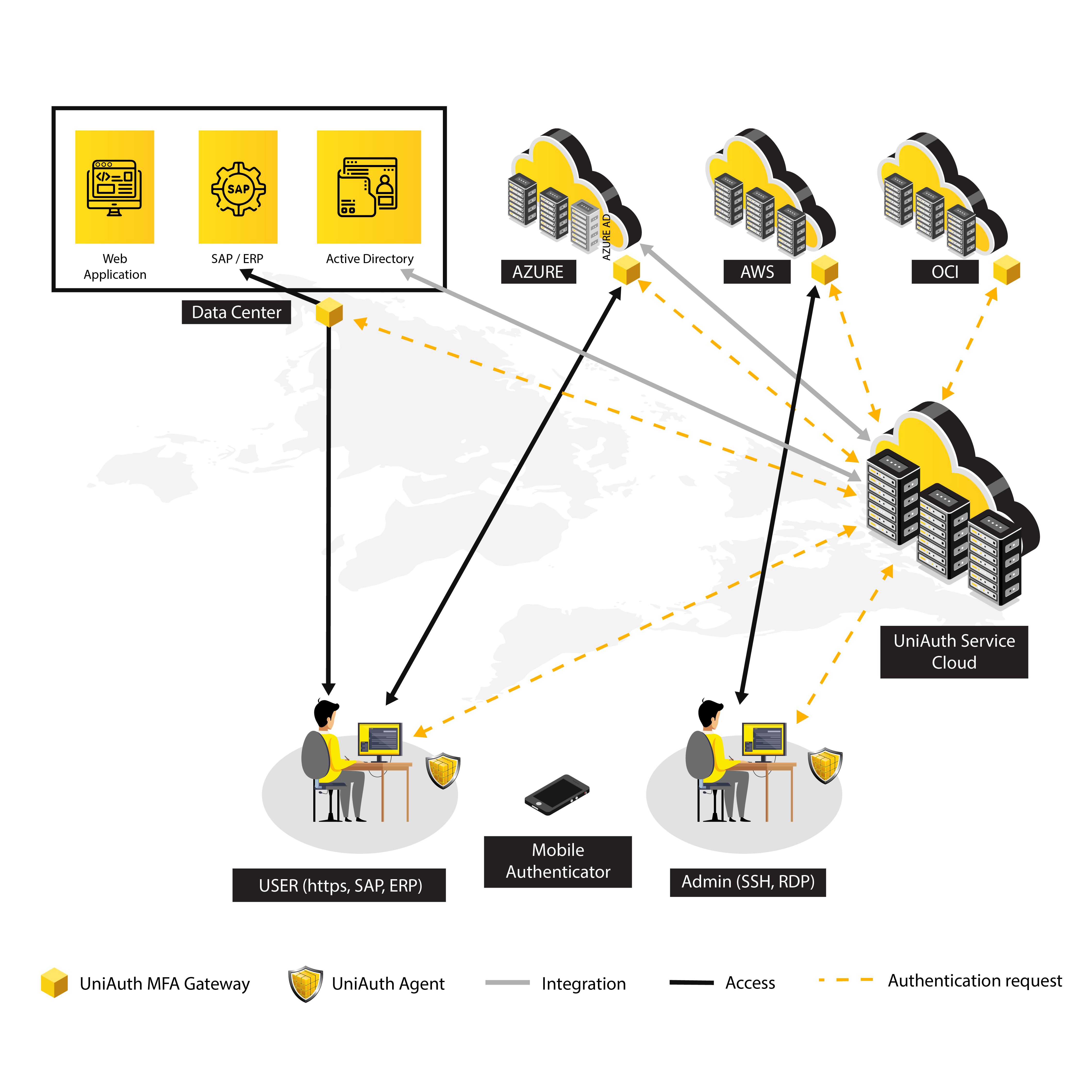
The only MFA built on Zero Trust principles.
Majority of breaches now originate with some form of credential compromise. Attackers have shifted focus to compromising user credentials as opposed to exploiting vulnerabilities or weaknesses in systems and applications.
Solution FlyerAccess |
Next-gen IoT Security
Smart, connected devices are already an integral part of our lives, in business and at home. And, with the advent of 5G and Satellite-based networks this will scale multi-fold. However, 5G Networks and the Internet of Things are opening up previously closed systems to remote access & control. And, existing security solutions are unable to keep pace, scale up and address the security challenges facing the emerging 5G and IoT world. Critical infrastructure incl. the Colonial Pipeline have suffered ransomware attacks while computer hackers have separately gained access to energy and utility grids and even tried to poison a water system in Florida.
BrochureAccess |
Smart CityInfographic |